Dev Team(s) Struggling with Security?
Let us help you reduce defects early in the software development life-cycle.
Thus significantly reduce costs downstream.
Helping you create and mentor security aware, cross functional, self-managing teams, able to create solutions that resist, and actively defend against today’s security attacks, while increasing profit and reducing costs.
Whether you’re running a small or large project, we can work with you to move the information security focus from late in the development life-cycle to within the development team. Thus saving significant costs, while improving quality, productivity, and predictability of software releases.
Be sure to review some of the clients we’ve worked with to establish successful outcomes, along with their testimonials
Services
What Differentiates Us
If you are looking to reduce the number of security defects produced by your development team(s), and increase their productivity, BinaryMist can work with you to achieve this. We are focussed on helping you create value rather than trading time for money. Read what our customers say about us.
Bug Free Guarantee
For development work, we stand behind the software we produce. In-fact, we are so confident, that if you find a bug in the software we produce for you within six months (sometimes longer), we will fix it for free.
.js-id-productised-service
EpicLines
Motorhomes for the discerning
New Zealands Own Surf Accessories

PurpleTeam
Modern Development Teams move fast - Choose a Security Solution that can keep up.Automatable Security Regression Testing for your Applications and APIs.The CLI can be run manually which provides a dashboard, but it’s sweet spot is being inserted into Development Team’s build pipelines and run in headless (noUi) mode.

Pete Nicholls
Trineo

Trineo
Security threat model & roadmap
Development Team Security Teardown $995NZ + GST
We can provide insight into potential issues/defects that are not obvious with your Development Team(s):
• Development Process
• System Being Developed
Our Teardown can provide the needed visibility in order to make the improvements.

Development Team Security Roadmap $2995NZ + GST
Too many security defects in your Development Team(s) deliverables?
External security reviews too costly?
Let us create a security roadmap for your Development Team(s).
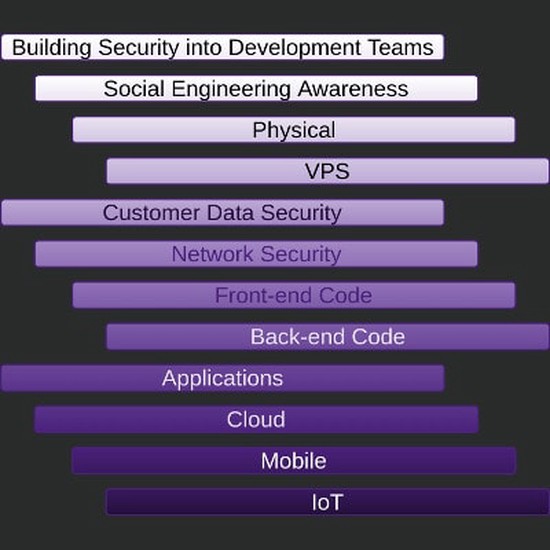
Security Strategy Retainer $3495NZ + GST
Our agreement entitles you to unlimited 1 on 1 access to Kim via phone, SMS, email, Slack, Skype, Signal, etc. Participation is limited to 10 people. Fee is for four months.

Building Security into Your Development Teams (workshop) $495 + GST per student
Full Day Interactive Workshop focussing on building security into your Development Team(s).

Christchurch Hacker Con
The third CHCon:
A conference aiming to raise awareness and skill levels of information security within our community.

Numisec Pte.
Security Review - Node.js Microservices

Stefan Streichsbier
Numisec Pte. Ltd
Mobiddiction
DevOps Implementation & Security Review

OWASP New Zealand Day
The ninth conference of its kind.
Dedicated to information security, with an emphasis on secure architecture and development techniques to help Kiwi developers build more secure applications.

Peter Montgomery
InventoryTech Ltd
MYOB
DevSecOps & AWS Migration

Lana Winders
SBS Bank

Rachel Robertson
SBS Bank
Development Team Security Implementation
Your Development Team(s) are struggling to create secure software. Your business is paying too much for security reviews, and penetration testing at the end of the project.
Your customers want to be certain that their personal data is secure. You could be saving significant expenditure on security and software development in general.
Security Review, Penetration Testing
You need to be sure that what your development team(s) are creating is going to withstand the onslaught of those tasked with breaking your deliverables, and stealing your customers data.
Your customers want to be certain that their personal data is secure. You need your product to stand-up to those that are going to attack it.

InventoryTech
Transitioning, architecture, & dev

Lentune
Architectural & Security Consulting

David Gadsby
Platinum Recruitment Ltd
SBS Bank
Personal Internet Banking

Andrew Balfour
Solvam Corporation Ltd
School-Links
Process Improvement. Back End Re-Architect

Hindin Solutions
Architectural Consulting & Development
Pivot Software
Architectural Consulting
King’s Church
Security Assessment

Christchurch City Council
Integration Development

Engela Pretorius
Christchurch City Council

Ming Yii
Christchurch City Council

Glen Senior
TSBC

Joe Kearns
Double-O Consultants

James Pinamonti
IAG, New Zealand
Recent Publications
Purchase Book Kim's Other Books Workshop Talk Podcast Blog Post Docker Cheat Sheet
Projects

EpicLines
Motorhomes for the discerning
New Zealands Own Surf Accessories

PurpleTeam
Modern Development Teams move fast - Choose a Security Solution that can keep up.Automatable Security Regression Testing for your Applications and APIs.The CLI can be run manually which provides a dashboard, but it’s sweet spot is being inserted into Development Team’s build pipelines and run in headless (noUi) mode.

Pete Nicholls
Trineo

Trineo
Security threat model & roadmap

Development Team Security Teardown $995NZ + GST
We can provide insight into potential issues/defects that are not obvious with your Development Team(s):
• Development Process
• System Being Developed
Our Teardown can provide the needed visibility in order to make the improvements.

Development Team Security Roadmap $2995NZ + GST
Too many security defects in your Development Team(s) deliverables?
External security reviews too costly?
Let us create a security roadmap for your Development Team(s).

Security Strategy Retainer $3495NZ + GST
Our agreement entitles you to unlimited 1 on 1 access to Kim via phone, SMS, email, Slack, Skype, Signal, etc. Participation is limited to 10 people. Fee is for four months.

Building Security into Your Development Teams (workshop) $495 + GST per student
Full Day Interactive Workshop focussing on building security into your Development Team(s).

Christchurch Hacker Con
The third CHCon:
A conference aiming to raise awareness and skill levels of information security within our community.

Numisec Pte.
Security Review - Node.js Microservices

Stefan Streichsbier
Numisec Pte. Ltd

Mobiddiction
DevOps Implementation & Security Review

OWASP New Zealand Day
The ninth conference of its kind.
Dedicated to information security, with an emphasis on secure architecture and development techniques to help Kiwi developers build more secure applications.

Peter Montgomery
InventoryTech Ltd

MYOB
DevSecOps & AWS Migration

Lana Winders
SBS Bank

Rachel Robertson
SBS Bank

Development Team Security Implementation
Your Development Team(s) are struggling to create secure software. Your business is paying too much for security reviews, and penetration testing at the end of the project.
Your customers want to be certain that their personal data is secure. You could be saving significant expenditure on security and software development in general.

Security Review, Penetration Testing
You need to be sure that what your development team(s) are creating is going to withstand the onslaught of those tasked with breaking your deliverables, and stealing your customers data.
Your customers want to be certain that their personal data is secure. You need your product to stand-up to those that are going to attack it.

InventoryTech
Transitioning, architecture, & dev

Lentune
Architectural & Security Consulting

David Gadsby
Platinum Recruitment Ltd

SBS Bank
Personal Internet Banking

Andrew Balfour
Solvam Corporation Ltd

School-Links
Process Improvement. Back End Re-Architect

Hindin Solutions
Architectural Consulting & Development

Pivot Software
Architectural Consulting

King’s Church
Security Assessment

Christchurch City Council
Integration Development

Engela Pretorius
Christchurch City Council

Ming Yii
Christchurch City Council

Glen Senior
TSBC

Joe Kearns
Double-O Consultants

James Pinamonti
IAG, New Zealand
Portfolio

EpicLines
Motorhomes for the discerning
New Zealands Own Surf Accessories

PurpleTeam
Modern Development Teams move fast - Choose a Security Solution that can keep up.Automatable Security Regression Testing for your Applications and APIs.The CLI can be run manually which provides a dashboard, but it’s sweet spot is being inserted into Development Team’s build pipelines and run in headless (noUi) mode.

Pete Nicholls
Trineo

Trineo
Security threat model & roadmap

Development Team Security Teardown $995NZ + GST
We can provide insight into potential issues/defects that are not obvious with your Development Team(s):
• Development Process
• System Being Developed
Our Teardown can provide the needed visibility in order to make the improvements.

Development Team Security Roadmap $2995NZ + GST
Too many security defects in your Development Team(s) deliverables?
External security reviews too costly?
Let us create a security roadmap for your Development Team(s).

Security Strategy Retainer $3495NZ + GST
Our agreement entitles you to unlimited 1 on 1 access to Kim via phone, SMS, email, Slack, Skype, Signal, etc. Participation is limited to 10 people. Fee is for four months.

Building Security into Your Development Teams (workshop) $495 + GST per student
Full Day Interactive Workshop focussing on building security into your Development Team(s).

Christchurch Hacker Con
The third CHCon:
A conference aiming to raise awareness and skill levels of information security within our community.

Numisec Pte.
Security Review - Node.js Microservices

Stefan Streichsbier
Numisec Pte. Ltd

Mobiddiction
DevOps Implementation & Security Review

OWASP New Zealand Day
The ninth conference of its kind.
Dedicated to information security, with an emphasis on secure architecture and development techniques to help Kiwi developers build more secure applications.

Peter Montgomery
InventoryTech Ltd

MYOB
DevSecOps & AWS Migration

Lana Winders
SBS Bank

Rachel Robertson
SBS Bank

Development Team Security Implementation
Your Development Team(s) are struggling to create secure software. Your business is paying too much for security reviews, and penetration testing at the end of the project.
Your customers want to be certain that their personal data is secure. You could be saving significant expenditure on security and software development in general.

Security Review, Penetration Testing
You need to be sure that what your development team(s) are creating is going to withstand the onslaught of those tasked with breaking your deliverables, and stealing your customers data.
Your customers want to be certain that their personal data is secure. You need your product to stand-up to those that are going to attack it.

InventoryTech
Transitioning, architecture, & dev

Lentune
Architectural & Security Consulting

David Gadsby
Platinum Recruitment Ltd

SBS Bank
Personal Internet Banking

Andrew Balfour
Solvam Corporation Ltd

School-Links
Process Improvement. Back End Re-Architect

Hindin Solutions
Architectural Consulting & Development

Pivot Software
Architectural Consulting

King’s Church
Security Assessment

Christchurch City Council
Integration Development

Engela Pretorius
Christchurch City Council

Ming Yii
Christchurch City Council

Glen Senior
TSBC

Joe Kearns
Double-O Consultants

James Pinamonti
IAG, New Zealand
Recent Posts
Do you want to improve your information security skills and knowledge as a Software Engineer? Let’s all learn together. At BinaryMist we’re on a continual learning journey and keen to share our learnings with you. Subscribe to new blog posts here.
Kim
The legacy BinaryMist blog is at blog.binarymist.net.
Talks & Workshops
Kim delivers high quality information security talks and workshops at conferences and private events around the world.

Most of Kims talks and workshops are focussed around demonstrating and demystifying how easy it is to break into software and networks, followed with how you can rectify the demonstrated vulnerabilities, and make this part of your development teams process, rather than finding and fixing the defects once in production. This has the benefit of saving significant expenditure due to finding and fixing defects late in the development life-cycle.
Presentation style
A huge amount of effort goes into Kims talks and workshops, continuing to refine his approach over time based on the feedback he receives. Kims talks and workshops usually contain a large amount of technical information coupled with an entertainment factor to help keep listeners and trainees engaged.
Speaking at your event
If you’d like Kim to speak at your event, get in touch via the contact section.
Running a workshop for you
If you’d like Kim to run a workshop at your event or private offices, get in touch via the contact section.
Recent and upcoming public Presentations and Workshops
Contact
- [email protected]
- (+64) 274 622 607
- Christchurch, New Zealand,
- 24/7 for paying customers
- DM Us
- Skype Us
