Workshop - Init Security Titans
This workshop was specifically taylored to initialise, train, motivate, and empower the new Security Champions within Jade, to scale security capability within all Jade Development Teams.
With the primary objective of revealing the secrets of shifting the focus on security from late in the software development life-cycle to within the Development Teams.
Not only does this significantly reduce the number of security defects being pushed to production systems, but also significantly reduces the total cost of development.
Cheapest place to deal with defects
There have been many studies specifically looking at the costs of finding and fixing defects early, as opposed to the planning of how to fix defects once the product is delivered, or not planning at all.
The following table shows the average cost of fixing defects based on when they were introduced versus when they are detected. Putting these practises in the right order can reduce costs of fixing security defects by up to 100 times.
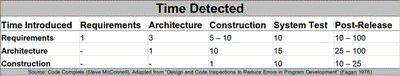
So… by simply shifting the security expertise from the end of the project to within the development team, thus enabling developers to find and fix their defects as they are being introduced, huge cost savings can be enjoyed.
This is not as difficult as you may think.
On the Day
Kim will lead the class through the tools, techniques and thought processes of both red (attacking) and blue (defending) teams along with how to combine these attributes into the purple team focussing on security, productivity, and tasked with continuously delivering sustainable maintainable technical solutions to market.
Kim will explain the roles of ‘T’ shaped professionals, including placement of security champions to create your purple Development Teams.
We will work through how to implement the Sensible Security Model (SSM) within each and every Sprint, including:
- Creating actionable countermeasure Product Backlog Items
- Integrating them into the same Product Backlog that your Development Team has been pulling business focussed items from
- Ordering them based on the risk ratings you create for each
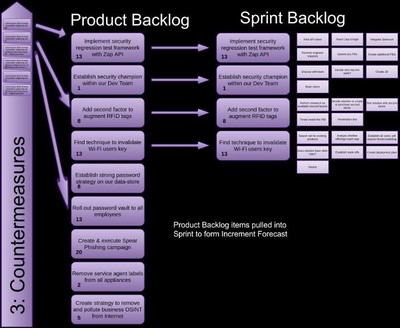
Kim will discuss how and where Agile Development Teams often fail, along with how to succeed with security with a familiar anecdote. Then augmenting your Scrum process within each and every Sprint, with a collection of development focussed processes and practises, tools and techniques that have proven their value at drastically reducing defects before production deployment.
Kim will walk us through the SSM threat modelling process with theory and hands on exercises in areas such as Physical, People, VPS, Network, Cloud and Web Applications. Including sub topics such as Docker, Serverless, PowerShell and many others.

More Detail
Training material will be augmented with Extracts from Kim’s interviews on Software Engineering Radio with security experts such as Diogo Mónica (Docker Security Team Lead) and Haroon Meer (creator of Canary tools and tokens).
Learnings
Coverage of topic chapters: