Workshop - Windows Exploitation and Persistence with PowerShell
Abstract
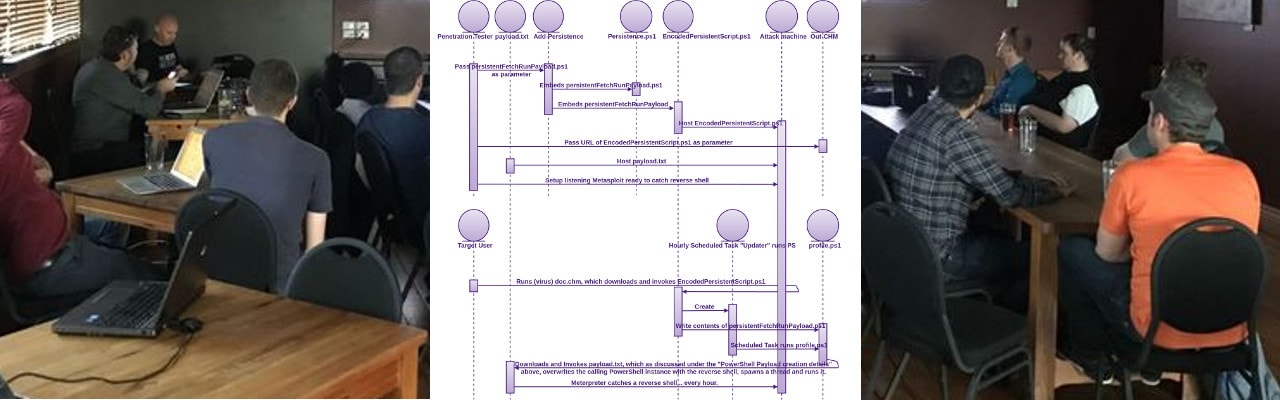
Kim will walk us through a collection of PowerShell delivery (RAM, not disk) techniques for a common reverse shellcode.
Date
Jan 25, 2017 19:30 PM — 21:00 PM
Event
Information Security Interest Group (ISIG)
Location
Christchurch, New Zealand
The common payload takes the user supplied shellcode and overwrites the first 0x1000 bytes of the calling instance of PowerShell, creates a thread to execute within the virtual address space of the calling PowerShell instance and starts it.
All delivery and persistence techniques ensure AV bypass of shellcode.
Kim has dissected and will explain how the virus and payload works.
We will look at delivery mediums (virus):
- Compiled C executable
- Office document (take your pick) C/- Nishang
Persistence mediums:
- Meterpreter (busted by AV)
- PowerSploit
Bring your pentesting devices if you want to do this workshop style, and we can do hands on.